What Is Credential Stuffing?
There are so many keywords and topics when it comes to cybersecurity that it is hard to keep everything straight. We hear about hacks, phishing, breach, ransomware, malicious emails, as well as so many more. One topic you may not hear often is Credential stuffing. Credential stuffing is the automated insertion of stolen username and password pairs (“credentials”) into website login forms to fraudulently gain access to user accounts. Credential Stuffing is a subset of the brute force attack category. Brute forcing will attempt to try multiple passwords against one or multiple accounts, guessing a password, in other words. Credential Stuffing typically refers to specifically using known (breached) username/password pairs against other websites.
Although we harp on not reusing passwords, many users continue to reuse the same password and username/email. So, when those credentials are exposed (by a database breach or phishing attack, for example), submitting those sets of stolen credentials into dozens or hundreds of other sites can allow an attacker to compromise those accounts too.
Credential stuffing is one of the most common techniques to take over user accounts. Credential stuffing is dangerous to both consumers and enterprises because of the ripple effects of these breaches. Let’s take a closer look at how credential stuffing occurs.
What are the steps of a credential stuffing attack?
- The attacker acquires usernames and passwords from a website breach, phishing attack, password dumpsite.
- The attacker uses automated tools to test the stolen credentials against many websites (for instance, social media sites, online marketplaces, or web apps).
- If the login is successful, the attacker knows they have a set of valid credentials.
The attacker now knows she has access to an account. What may happen next…
- Draining stolen accounts of stored value or making purchases.
- Access sensitive information such as credit card numbers, private messages, pictures, or documents.
- Using the account to send phishing messages or spam.
- Selling known-valid credentials to one or more compromised sites for other attackers to use.
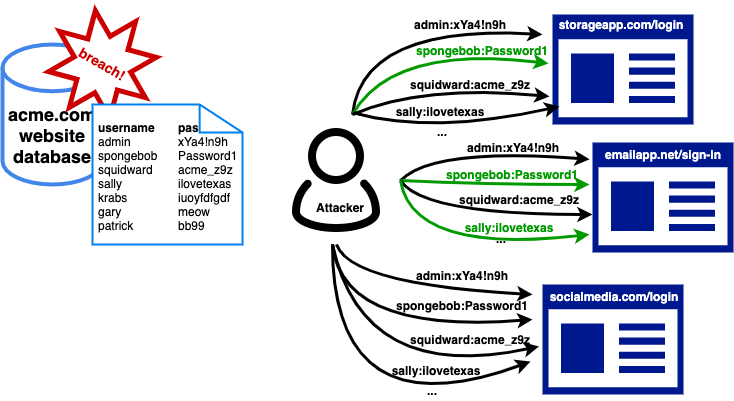
In the diagram above, you can see that acme.com’s database was compromised. The attacker then takes the breached database and tries the credentials on three other websites, searching for successful logins. The attacker verifies two websites where the user “Spongebob” is reusing their password and one website where the user “sally” is reusing their password. The attacker can now get access to those three accounts.
As you can see, credential stuffing is an effortless way for hackers to data. It is essential to consider how many of your employees potentially use the same usernames and passwords for websites linked to their private lives and business. If there is a breach, all of these accounts are at risk. To learn more about how to prevent credential stuffing, be sure to read next week’s blog and, as always, reach out to your Pendello Solutions team today.
At Pendello Solutions, we turn technology hurdles into powerful assets. Our technology solutions fuel growth, productivity, and efficiency, through continuous innovation and strategic solutions, empowering your business beyond the imaginable. Contact us today to discover the Pendello Method.
