The Dark Web Uncovered
Picture this: You’re on an e-commerce website you haven’t shopped on before and you’ve got a couple of nice-looking items in your cart—but you’re debating whether or not to hit that shiny “place order” button. The stuff looks good, but you’re not quite convinced yet. So, you decide to do some quick research on the company and its products.
You read more about the company’s history, and your heart swells when you learn that the company got its start when its three founders were only teenagers (what entrepreneurship!). They seem to have a pretty solid business model, and no major red flags are jumping out as you hop around the site a bit more.
You then discover there’s a happiness guarantee with your purchase—if you’re not satisfied, they guarantee to make it right. In fact, there’s a button to the bottom right of the screen to reach out to customer service should you experience any issues.
To sweeten the deal even more, a pop-up notes that the price of the product is negotiable. Who doesn’t love the chance to bargain for a good deal?
Things seem to be looking good, and it’s time to go ahead and place that order—right?
What if I told you I just described an experience over the dark web?
That’s right—today’s shady websites and dark web marketplaces operate in such a way that they’re starting to resemble the very same sites we use to buy perfectly legitimate items.
No longer are hackers the hoodie-donning, mask-wearing teenagers camping out in the dark in their parents’ basements. Today’s hackers work just like many of us—in a role in a department at a company, clocking out just like we do at the end of the day.
There’s no doubt you’ve heard of the dark web before—but have you actually been there? In this blog, we’ll be your tour guide as we take a plunge into the darkest corners of the web that account for only around 5% of the total internet. Get ready for a wild ride, because some of what we’ll see during our journey might surprise you. 😳
What Is the Dark Web?
Everyone has their own preconceived notion of what the dark web is. (Of course, with a name as ominous as dark web, it’s hard not to.) For the sake of this blog, we want to hone in on a credible definition that isn’t muddied with preconceptions. So, we turned to the dictionary.
The Merriam-Webster online dictionary defines the term dark web with the following definition:
The set of web pages on the World Wide Web that cannot be indexed by search engines, are not viewable in a standard Web browser, require specific means (such as specialized software or network configuration) in order to access, and use encryption to provide anonymity and privacy for users.
(If you were expecting a more sinister-sounding definition for the term dark web, you’re not alone. 😅)
How Does the Dark Web Work?
Frankly, the dark web has earned a bad reputation—and rather unfairly so. At its core, the dark web isn’t inherently dangerous or shady.
It’s simply a collection of websites that require a specific, anonymity-powered web browser to access. Usually, these sites feature a .onion domain and are accessed through the anonymous Tor Browser.
The dark web has perfectly legal and legitimate purposes. For instance, detectives and journalists sometimes access the dark web to do research while maintaining their anonymity. You can play chess on the dark web. At one point in time, you could even navigate to a Tor website and watch a slideshow of cats and kittens submitted by other users.
The dark web really is what you make of it.
The Dark Side of the Dark Web
Alas, there is a dark side to the dark web. Look no further than hackers for one such example.
Hackers use the dark web as their playground to sell their services and earn a living. The buyer’s journey described at the beginning of this blog is very much a real depiction of what you may stumble across when browsing the dark web. Hackers are out to earn a living, and they have to market themselves, their expertise and their services just like any salesperson does to make a sale.
But what do these sites look like? Can you really click around and navigate to reviews, mission statements, guarantees and customer service just like you can any other e-commerce website?
Yes, you can.
There’s a light side and a dark side to the dark web. We’re going to explore the dark side in this blog. 😈
What Does The Dark Web Look Like?
(Note: Click any of the images throughout this blog to enlarge them.)
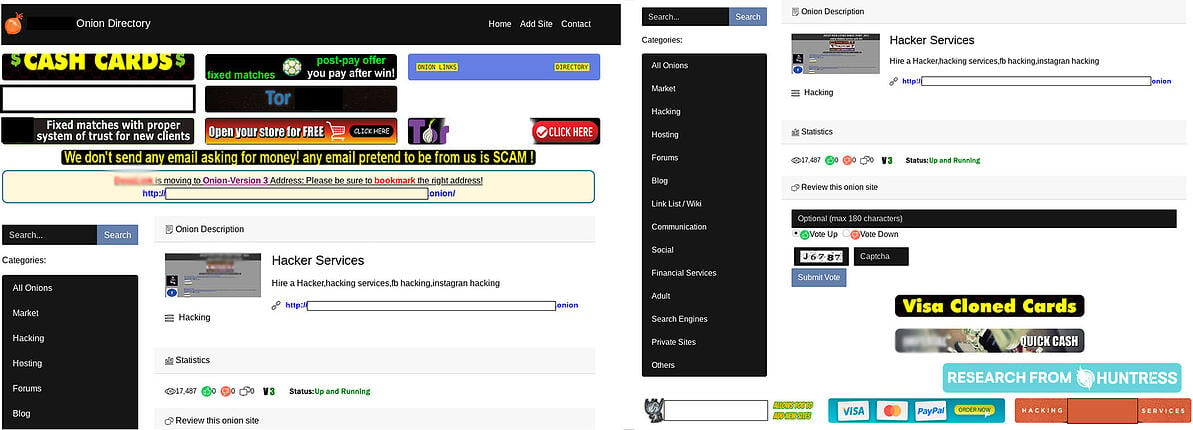
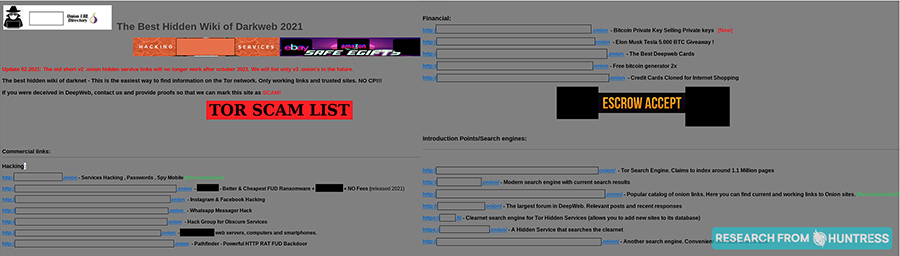
Check out this golden egg: a Tor scam list along with recommendations on “safe” sites to browse. How thoughtful.
Who Are These Hackers on the Dark Web?
There are About Us pages to answer that question.
Chances are you wouldn’t hire a plumber without doing some research. You’d want to make sure she’s got the experience and skills to leave your pipes in a better shape than she found them. By that same token, why would anyone hire a hacker without seeing a thoroughly written About Us page?
You might think this requirement would narrow the pool of hackers to choose from because are hackers really spending their time writing About Us pages? Yes, they are.
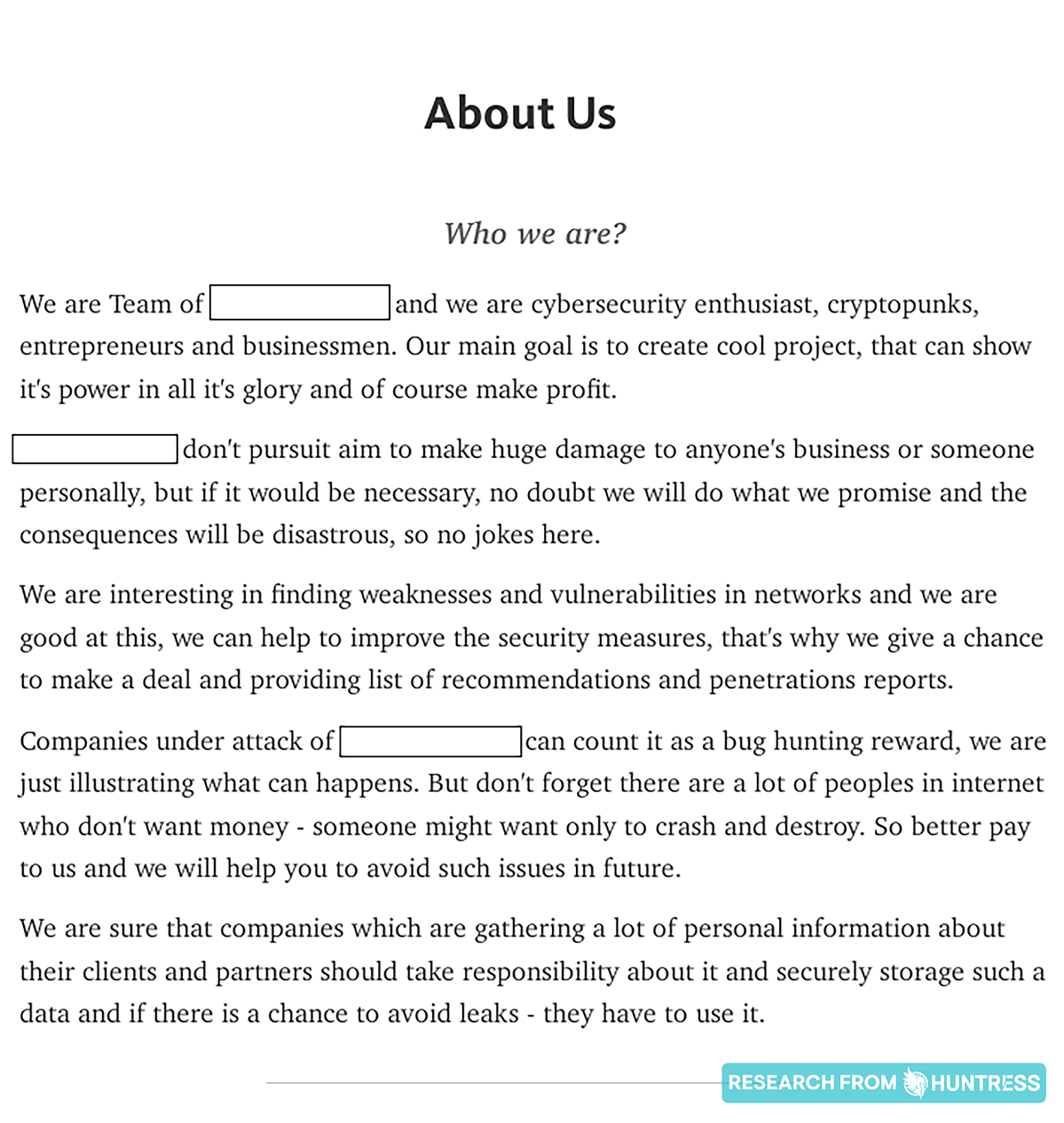
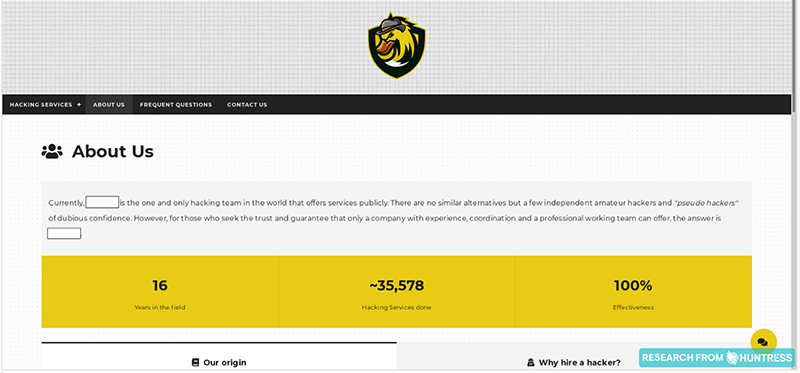
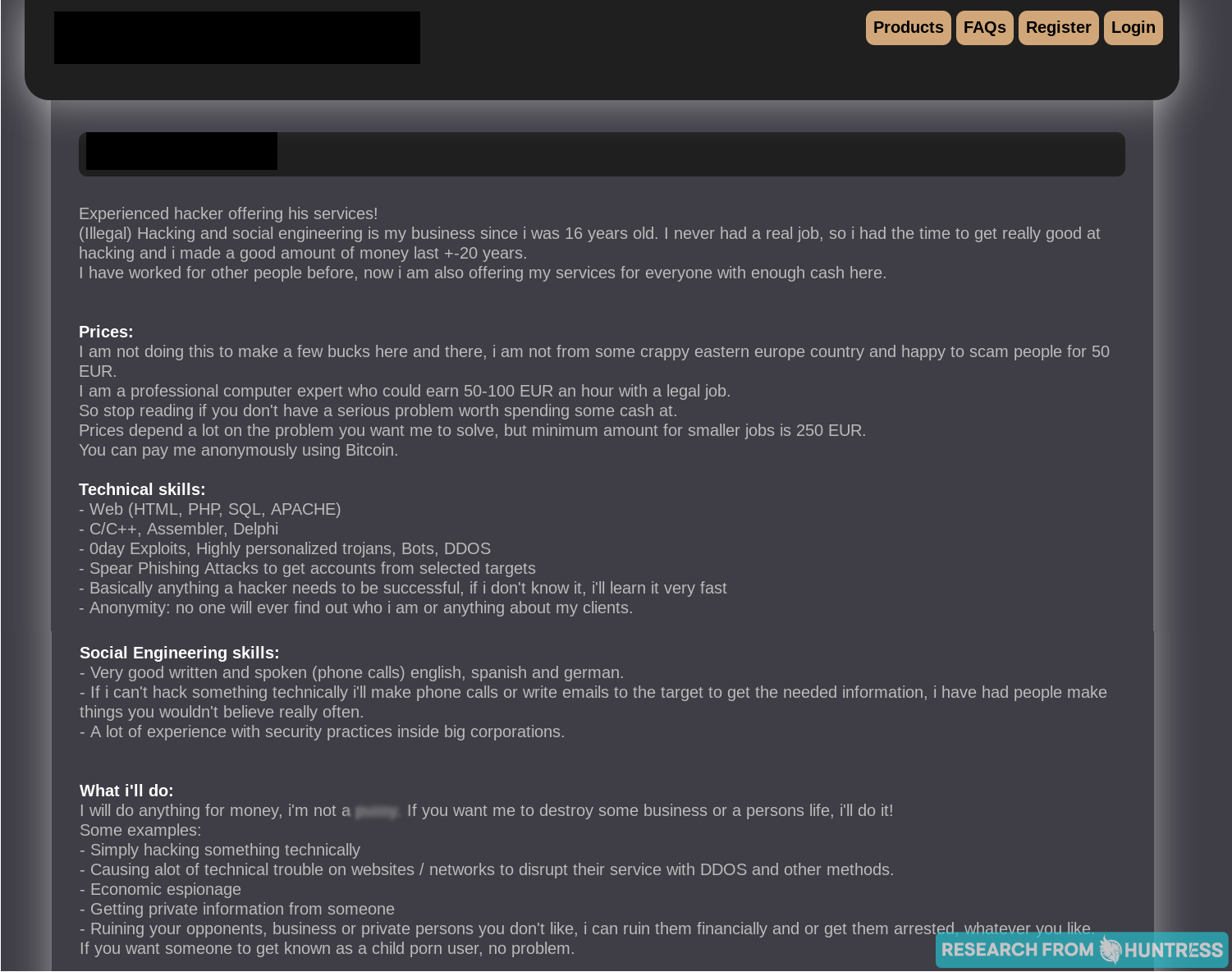
You’ve got to hand it to them: these hackers did a great job at flexing their hacking skills while remaining anonymous. While it isn't LinkedIn, there’s just enough information on these About Us pages to give these folks some credibility (in a strange way).
If you’ve never browsed the dark web before, you probably weren’t expecting to see several websites with About Us pages. It’s eye-opening to see these hackers flaunting their skills and competing with one another to earn new business.
One site was even gracious enough to list the team’s favorite well-known hackers:
It’s kind of sweet, in a weird sort of way.
The takeaway: Hackers are just like any other entrepreneurs out to make a quick buck. The key difference is that hackers don’t have to deal with the stipulations and regulations that other entrepreneurs must abide by. This leaves the door wide open for hackers to advertise whatever services they please—as long as they abide by the Hacker’s Code of Conduct. (More on that later.)
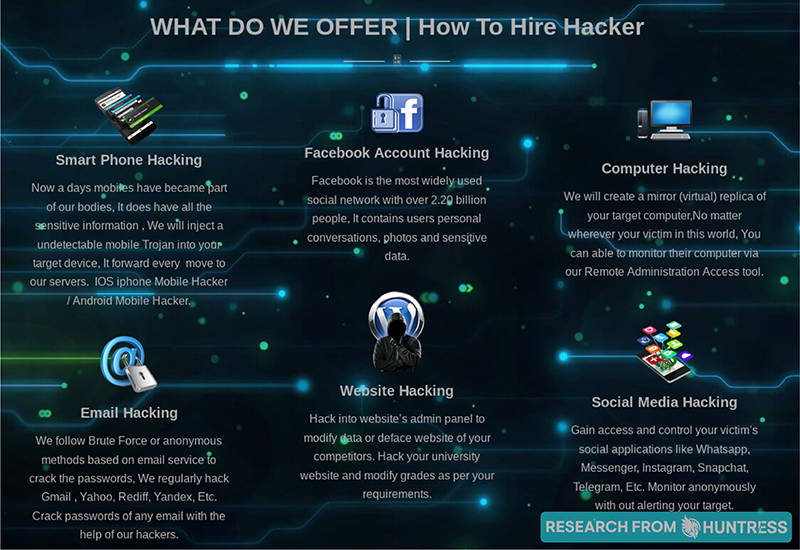
Hacking Services on the Dark Web
Product pages, packaged deals and more.
Now that we know our hackers, let’s investigate what they can do for us.
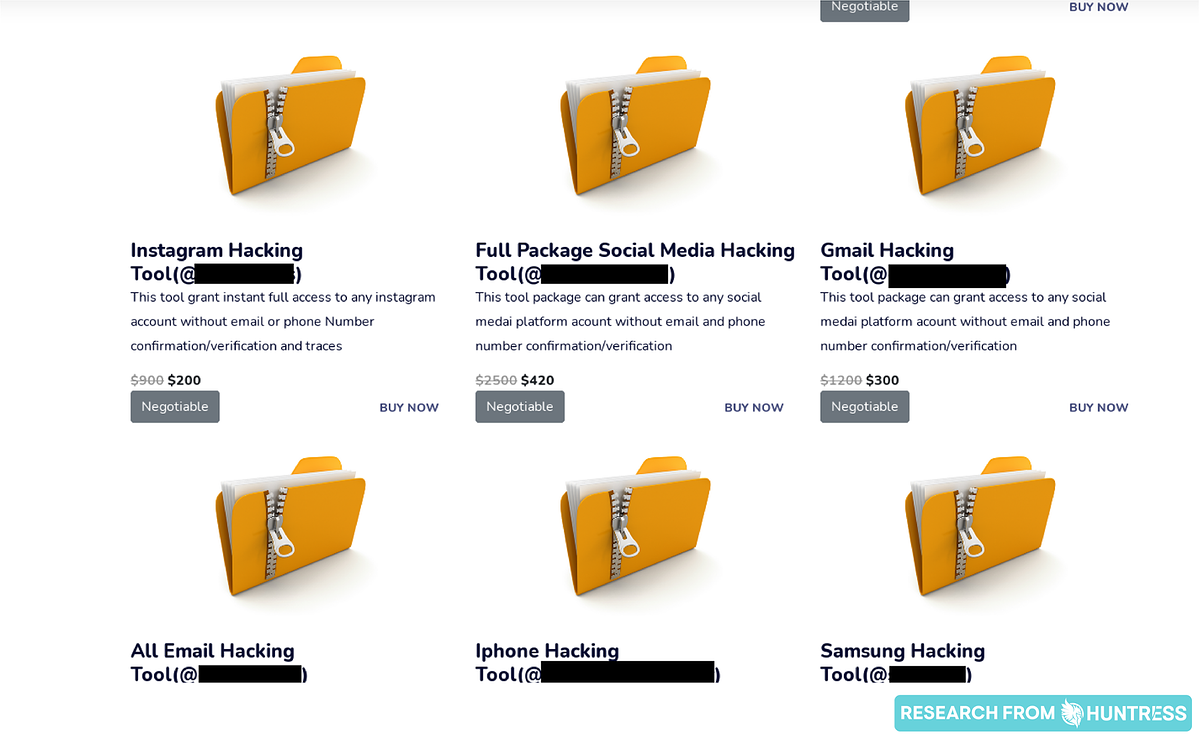
Like any good businessperson, hackers aren’t shy about broadcasting what they can do if the price is right. In fact, some hackers are so business-savvy that they provide packages and tiered solutions: 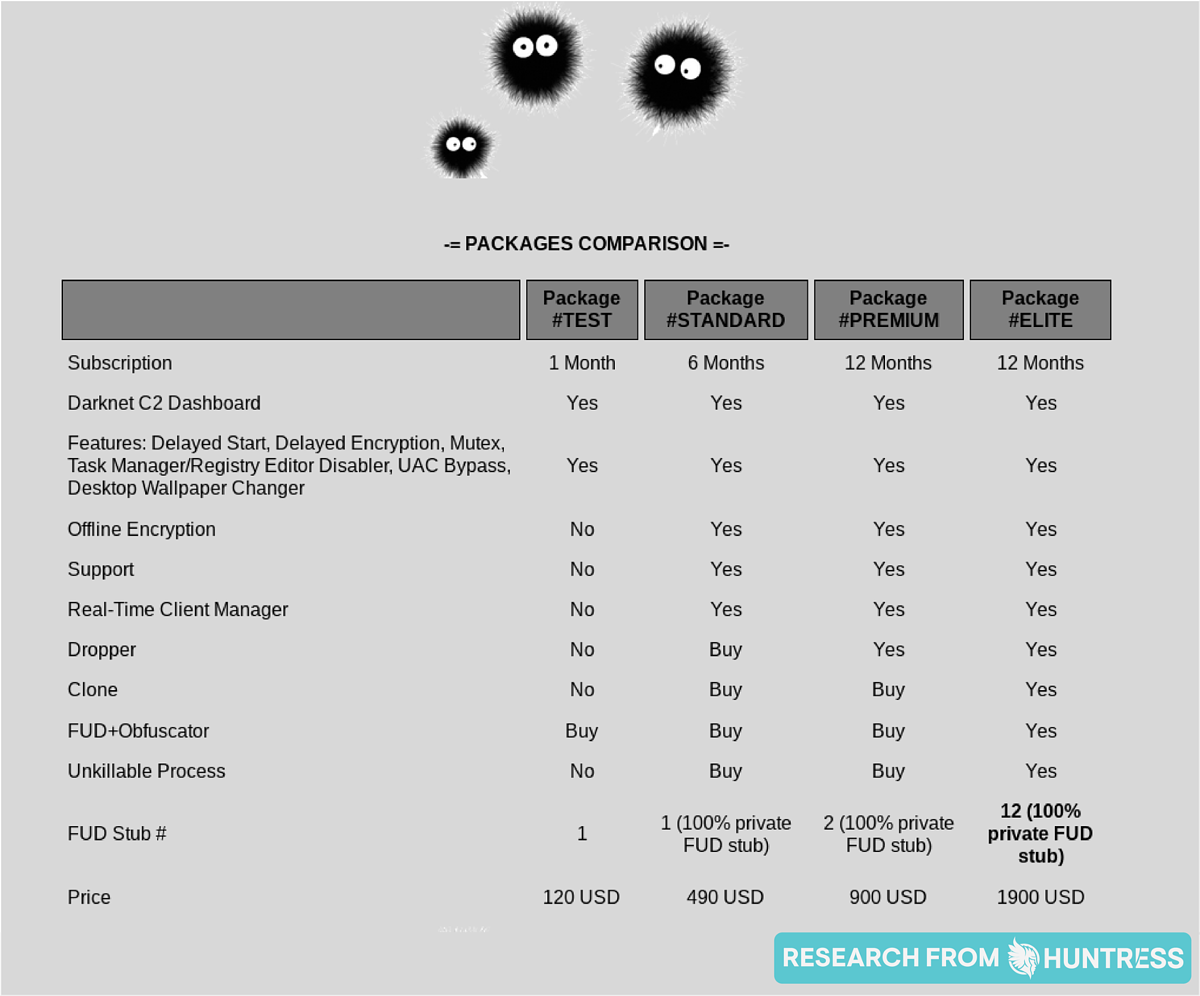
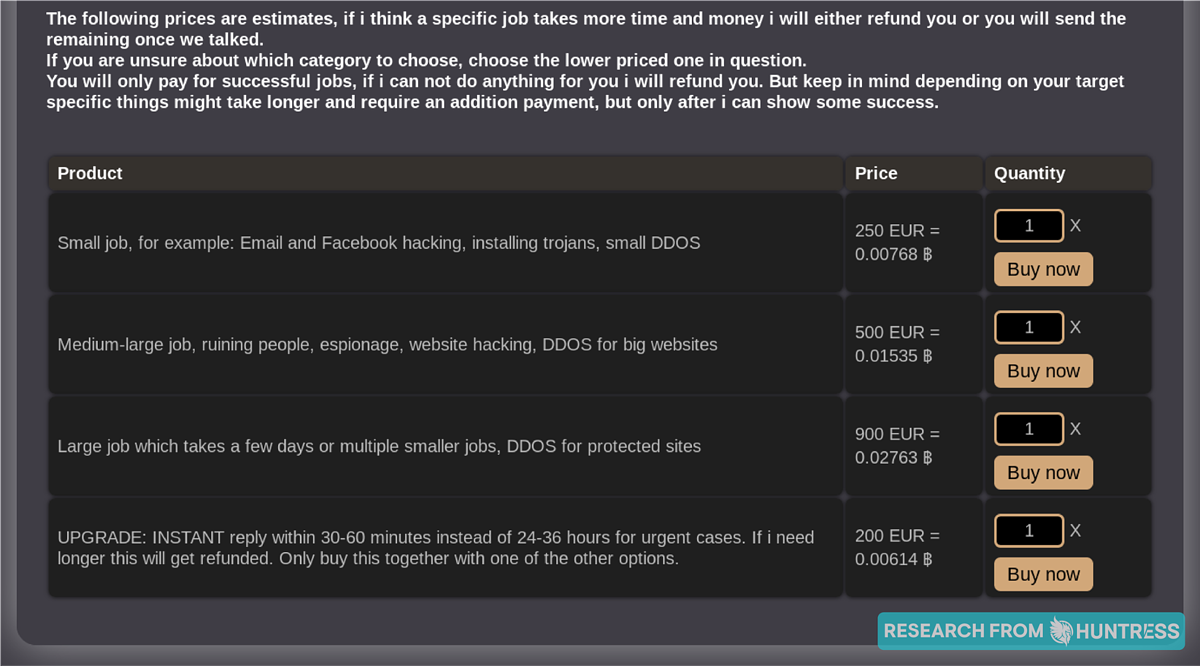
Others simply prefer to put all their services out there for people to pick and choose from:

The takeaway: Just like any other website where you can purchase products or services, hackers also have tiered options, promotional packages and detailed descriptions of their offerings.
One key difference that seems to be standard across dark web websites is that hackers request that their payments be made in cryptocurrencies. Why? For the same reason these hackers hang out on the dark web: it’s anonymous.
Our Senior Security Researcher, John Hammond, nicely sums up why cryptocurrencies are a hacker’s best friend:
"No other technology offers a bad actor the perfect crime: anonymous threats without borders, blackmail and extortion without a financial oversight or governing authority. [...] Unless the bad actors make any unintentional mistake, the inherent design of cryptocurrency makes for a perfect getaway car."
Customer Experience
Chat features, referrals and negotiable prices.
If you think that hackers aren’t concerned about the buyer’s journey, think again.
The customer experience seems to be a top priority on many of the hacking sites we’ve come across.
And just about every website we came across featured a Frequently Asked Questions section for easy reference:
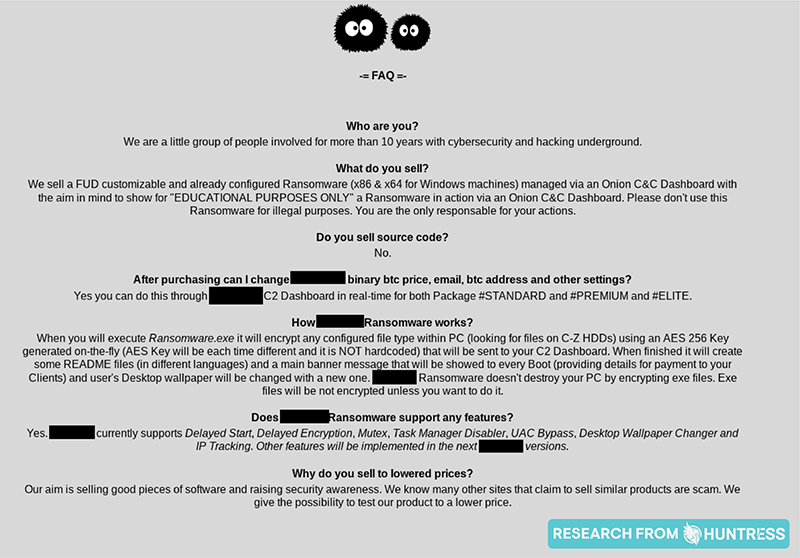
The takeaway: From referral bonuses to always-on availability, hackers seem to take care of their customers. They make it easy to find answers to prospective customers’ frequently asked questions, and just about any information you’d need to make an informed decision is available on each website. Truly, many of their customer service practices have achieved a level that some legitimate businesses can only dream of reaching.
Customer Reviews and Testimonials
Product reviews and testimonials from satisfied customers.
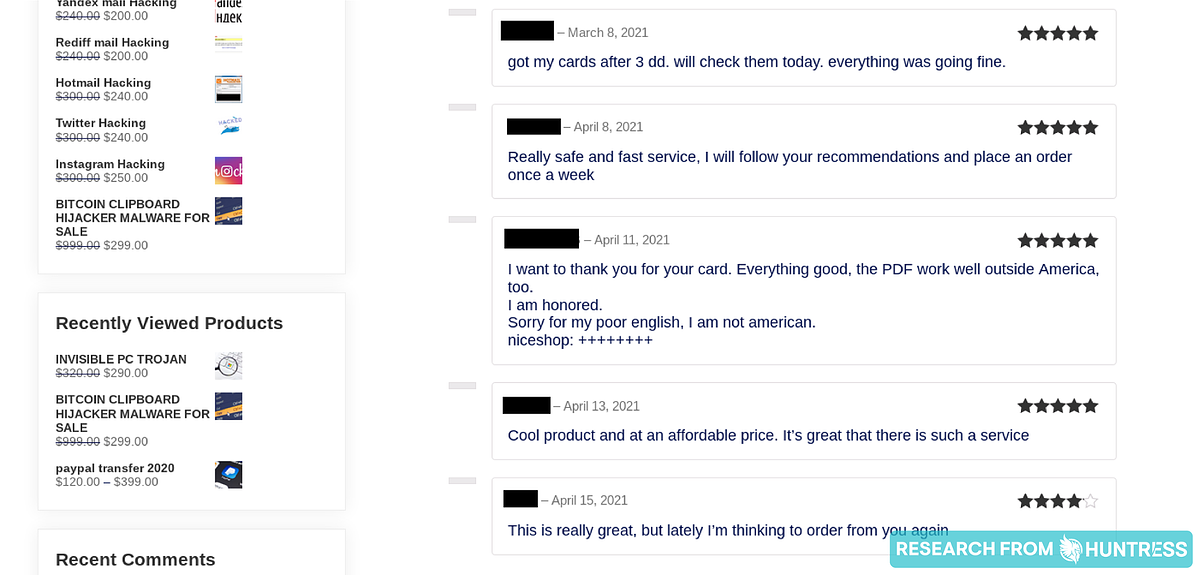
Word of mouth is a powerful sales technique. A collection of customer reviews and testimonials can function as a powerful driver to convert a prospect into a customer. Hackers, who have already proven their business finesse, seem to embrace this, as seen on several of the websites we explored:
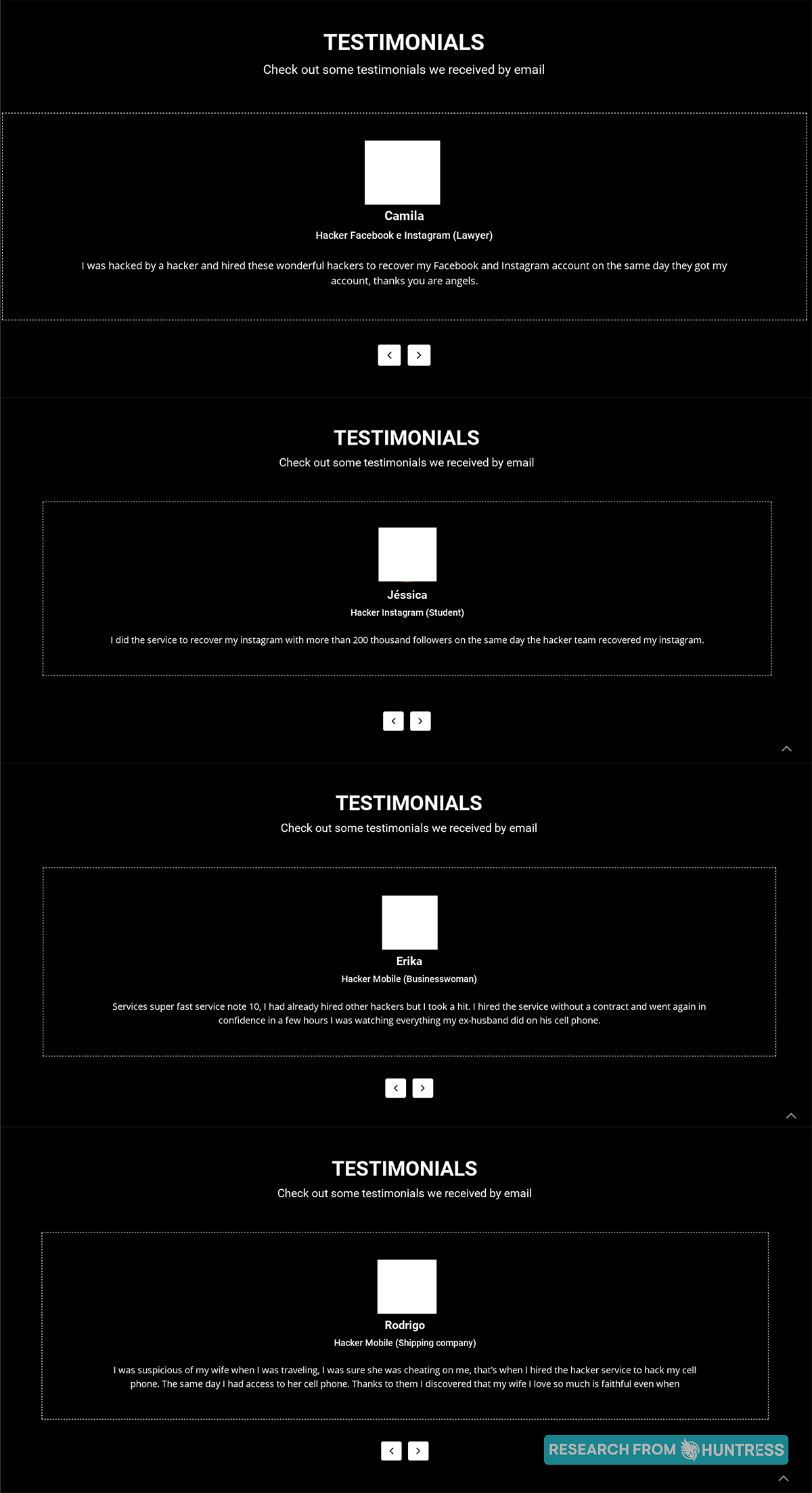
(We’re quite upset that Rodrigo’s review ended abruptly.)
The takeaway: Just like any other website with goods and services for sale, hackers too want to show that they have happy customers.
It’s one thing to see hackers going into detail about the services they offer. It’s almost something from another realm to see reviews with people bragging about how the hackers did a great job of helping them track the cellphone activity of their spouses and exes.
The Hacker’s Code of Conduct
If a business owner feels she’s been wronged, there are courts for that. The same can be said for hackers. That’s right—hackers have their very own court system along with codes of conduct to follow to minimize the chances that they’ll end up there as a defendant.
Recently, DarkSide was taken to “hacker’s court” for not paying their affiliates following the Colonial Pipeline attack. What happens in “hacker’s court”? The same thing that happens in any other court: plaintiffs and defendants get together to tell their respective stories in front of a jury before a ruling is made. Even hackers have a sort of code of conduct to follow, and if they’re wronged, they can have their day in court.
We cannot stress this enough: most hackers today don’t simply hack into websites and devices for the fun of it. These are professionals who become experts in their trade and master their skills to earn a paycheck.
They build websites to sell their services, cut their customers special deals, and ask for reviews from satisfied customers. If they’re wronged, they go to hacker’s court. These are organized operations that function just like any other business.
Are You Afraid of the Dark (Web)?
We hope that this field trip to the dark web has been enlightening. It’s incredible to see just how many parallels exist between anyone with a “normal” day job and hackers. Many different careers, from marketing and sales to cybersecurity and infosec, have “dark side counterparts” that can be found punching in and out from their shifts on the dark web.
If nothing else, we hope this blog will make you more vigilant against cyberattacks. Hackers are often in it for the money. What could destroy your personal records or business’ reputation is a mere transaction for money to a hacker. Think twice before clicking on an email from an unfamiliar sender, keep your devices updated and install patches as soon as they become available. And, as always, when in doubt, reach out to your Pendello Solutions Team. Let us investigate anything suspicious!
At Pendello Solutions, we turn technology hurdles into powerful assets. Our technology solutions fuel growth, productivity, and efficiency, through continuous innovation and strategic solutions, empowering your business beyond the imaginable. Contact us today to discover the Pendello Method.
