Is There A Right Way To Set Up Two-Factor Authentication?
Lately, there's been a lot of chatter around two-factor authentication (2FA) and multi-factor authentication (MFA). We're seeing more and more websites and applications enforcing 2FA—like Google recently announcing 2FA will be turned on by default for all accounts. But that led us to wonder: How easy is it for malicious threat actors to circumvent 2FA?
What Is 2FA?
Two-factor authentication is a verification method that requires users to provide at least two forms of identification to access something.
Rather than just asking for a username and password, 2FA requires an additional verification factor, decreasing the likelihood of a successful cyberattack. These factors can include:
- Knowledge (something only the user knows)
- Possession (something only the user has)
- Inherence (something only the user is)
- Location (somewhere only the user is)
Why Is 2FA Used?
When you think of authentication, you probably think of the typical username and password (that's the single factor). But as we all know, those passwords can easily be stolen, shared, reused, or compromised somehow.
Instead of relying on a single factor, 2FA adds an additional layer of security by requiring another or multiple forms of authentication—in theory, making it harder for hackers and unauthorized users to gain access to your accounts or devices.
How Attackers Bypass 2FA
Because two-factor authentication adds that extra layer of security, many people assume that makes it impenetrable. But, like almost anything these days, 2FA can be bypassed.
Let's dive into just how easy it is to bypass 2FA. For this example, we're only going to pick on SMS-based authentication, which is a method that allows users to verify their identities with a code that is sent to them via text message.
The SIM Swapping Problem
As the avid cell phone and smartphone users that we all are, we know how phone carriers want to provide their customers with the best customer service. Unfortunately, hackers can easily exploit that need to please.
The image below illustrates how attackers can trick phone carriers through SIM swapping. In a nutshell, SIM swapping is when a scammer steals your mobile phone number by assigning it to a new SIM card. By calling up your carrier's customer service line and giving a few details about you, a hacker can claim that your original phone and SIM card were lost or destroyed and have a new SIM card they'd like to activate.
Here's a look at SIM swapping in action:
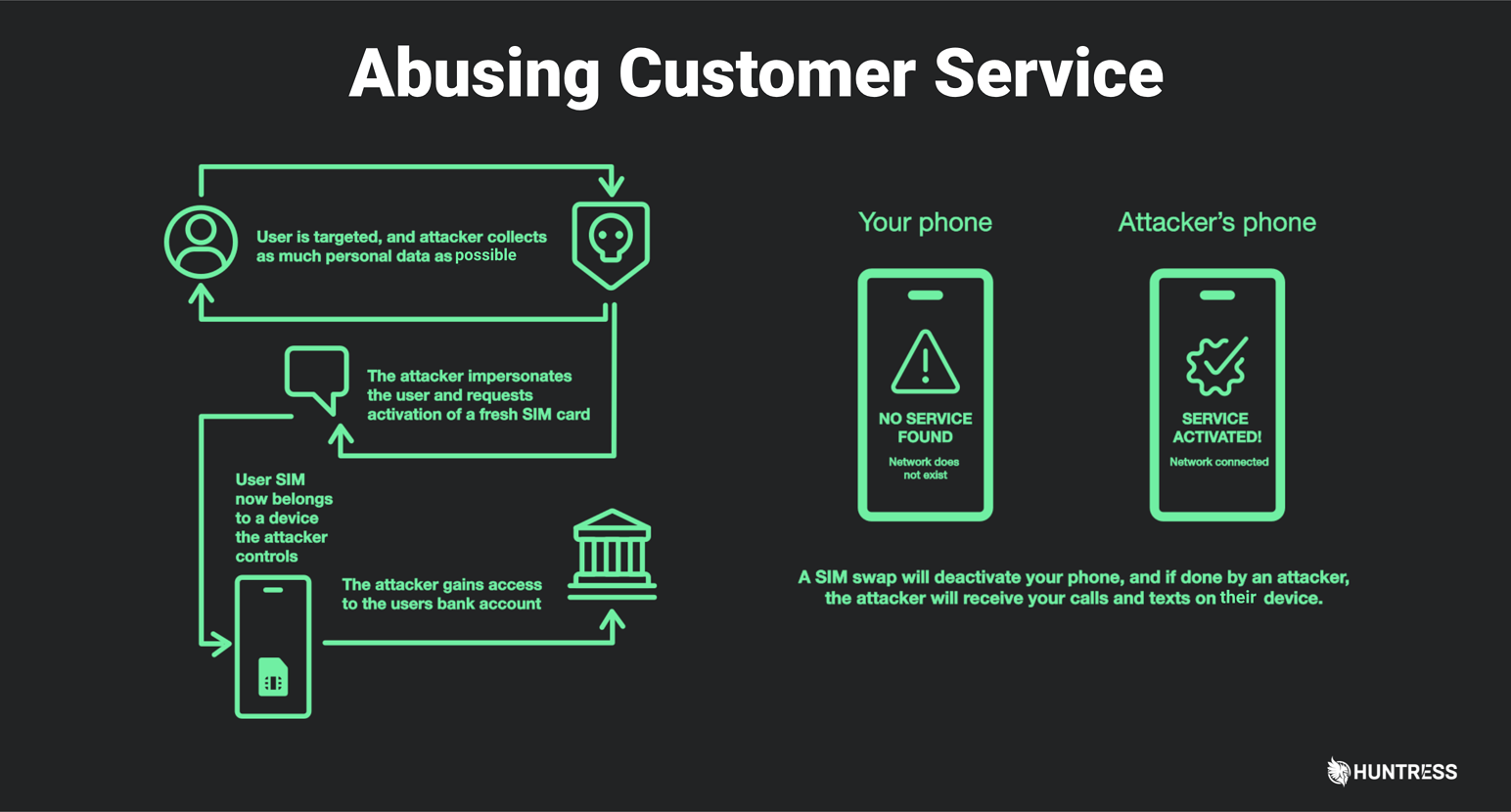
Let's put this into the context of SMS-based 2FA. Can you see why SIM swapping could be a huge issue?
Suppose an attacker knew your username and password and successfully tricked your carrier into a SIM swap once they entered your credentials now. In that case, they receive the authentication code via text message, and BOOM, they're in. That so-called second factor is now bypassed because people are way more exploitable than technology.
Please note: We're not trying to strike fear into your heart. The most common targets of SIM swapping are celebrities, politicians, or Fortune 500 CEOs—but what we are trying to emphasize is that in this case, the security of your SMS authentication relies on the safety of a third-party carrier, or lack thereof.
Is 2FA Worth Setting Up?
Yes, 100% it is. Layers are so important, and 2FA is another layer in your defense against attackers… but as we've seen, it isn't perfect.
Our example showed just how bypassable SMS-based authentication is through SIM swapping or social engineering phone carriers. It's clear that hackers are growing more sophisticated every day—with small amounts of information, there's a lot of damage they can do. So, if possible, avoid SMS-only authentication when you're setting up 2FA.
And, of course, there's the convenience argument. Some users will complain that 2FA is a pain because they need to take another step to log in. That's understandable, but cybersecurity is always a trade-off. Given the sheer cost of security incidents today, a few extra steps are much less painful than dealing with a cyberattack.
And if there are a few key lessons we can leave you with, it's these:
- Enable 2FA or MFA wherever possible. In addition to educating users to use unique passwords for each application, this will reduce their account's chances of being compromised.
- Leverage SSO with 2FA. This allows you to have a central location to disable user access.
- Educate your users on the benefits of using 2FA. Understanding the trade-offs may make the extra step less painful for users. And while we're at it, remind users not to provide their 2FA tokens to anyone else.
Now, if you have any additional questions on MFA and why it is essential, contact your Pendello Solutions team today!
At Pendello Solutions, we turn technology hurdles into powerful assets. Our technology solutions fuel growth, productivity, and efficiency, through continuous innovation and strategic solutions, empowering your business beyond the imaginable. Contact us today to discover the Pendello Method.
